How to Change OS TCP/IP Fingerprint
Some useful info & tips on OS TCP/IP Fingerprint.
Passive OS TCP/IP Fingerprinting, how it works
Client opens a connection, sends TCP SYN, and somebody inbetween analyzes it. This technique is named p0f. Only TCP SYN is unique for each OS, so OS name & version & even uptime can be extracted from it. In particular:
- ip ttl (p0f3: ittl)
- tcp mss (p0f3: mss)
- tcp options sequence (p0f3: olayout)
- tcp window size (p0f3: wsize)
- tcp window scaling (p0f3: scale)
- tcp quirks
More read: https://github.com/laoshaw/p0f3 => scroll down to “== TCP signatures ==”
All subsequent packets from client to the server are not unique: TCP ACK,RST,FIN etc.
Uptime is detected by a TS (timestamp) option in tcp options sequence, which contains 2 values, and TSval correlates with uptime.
Active OS TCP/IP Fingerprinting, how it works
Attacker (well, it is not an attack, but anyways) sends a TCP SYN to the object, connection established, TCP SYN+ACK is sent back & analyzed by the attacker. The same factors do matter as for TCP SYN, but signatures do differ.
Software used for p0f (CLI)
- https://github.com/MOL0ToK/sp0ky
- https://github.com/cesarghali/OS-Fingerprinting
- https://github.com/laoshaw/p0f3
- https://github.com/NikolaiT/zardaxt
- tcpdump / tshark (for checking raw signatures)
WEB services for p0f
Those use p0f3 or very similar:
http://witch.valdikss.org.ru/- https://browserleaks.com/ip
- https://whoer.net - click “Extended version”
Uses its own set of signatures:
https://tcpip.incolumitas.com/classify?by_ip=1
Databases of signatures
https://raw.githubusercontent.com/laoshaw/p0f3/master/p0f.fp p0f3 , TCP:request + TCP:response
https://raw.githubusercontent.com/xnih/satori/master/fingerprints/tcp.xml p0f1 , TCP:request
https://raw.githubusercontent.com/NikolaiT/zardaxt/master/database/combinedJune2022.json kind of p0f1 format , used in Incolumitas checker.
Problem:
-
p0f3 database (not mentioning the p0f which is even more old!) is very outdated and don’t reflect modern situation with modern devices. For example, if you want to spoof TCP/IP fingerprint to pretent iOS, then even if you grab proper set of TCP options from real iOS, you still be recognized as
MAC OSX generic. There is only 1 entry for iOS in p0f3, and when you start emulating it, yes, you will be seeingiPad or iPhonebut it has a poor Wscale, so your connection will be starting too slowly. -
the same is for Android. There are just 2 records in p0f3 for Android. While real Androids are visible as
Linux genericor similar. -
For Windows. p0f3 doesn’t have records for modern Windows versions, they are detected as
Windows 7 or 8.
Solution
You have 2 solutions
-
Grab real TCP signatures from real devices and use them for TCP/IP OS spoofing. Pro: it will be real & genuine. Con: those public detectors will detect you as a wrong OS.
-
Use OS TCP signatures from p0f3. Pro: those public detectors will detect you as a target OS. Con: some private detectors still may detect you as a spoofer :-) And expect some speed losses because of non-optimal Wscale.
How to spoof OS TCP/IP Fingerprint? Theory.
- Linux Iptables firewall diverts outgoing TCP SYN packets to a local NFQUEUE
- A software opens a Netfilter Queue, which accepts TCP packets.
- unpacks them, adjusts mandatory TCP options, re-packs & sends
The software is scapy, a python module.
How to spoof OS TCP/IP Fingerprint? Practically.
There is a good easy to use software called OSfooler-ng + its many forks. It is abandoned now. Also it uses ancient p0fv1 database. Also it simply can’t process TS options which are VERY important for simulating MAC/iOS. In fact it is only useful for simulating Windows.
There is a python module scapy-p0f, which uses p0f3 database, but still can’t process TS options. Yet it doesn’t have a ready to use program.
So the solution would be to take OSfooler-ng, modify it, so it works with scapy-p0f. I have done it, please DM me!
Result
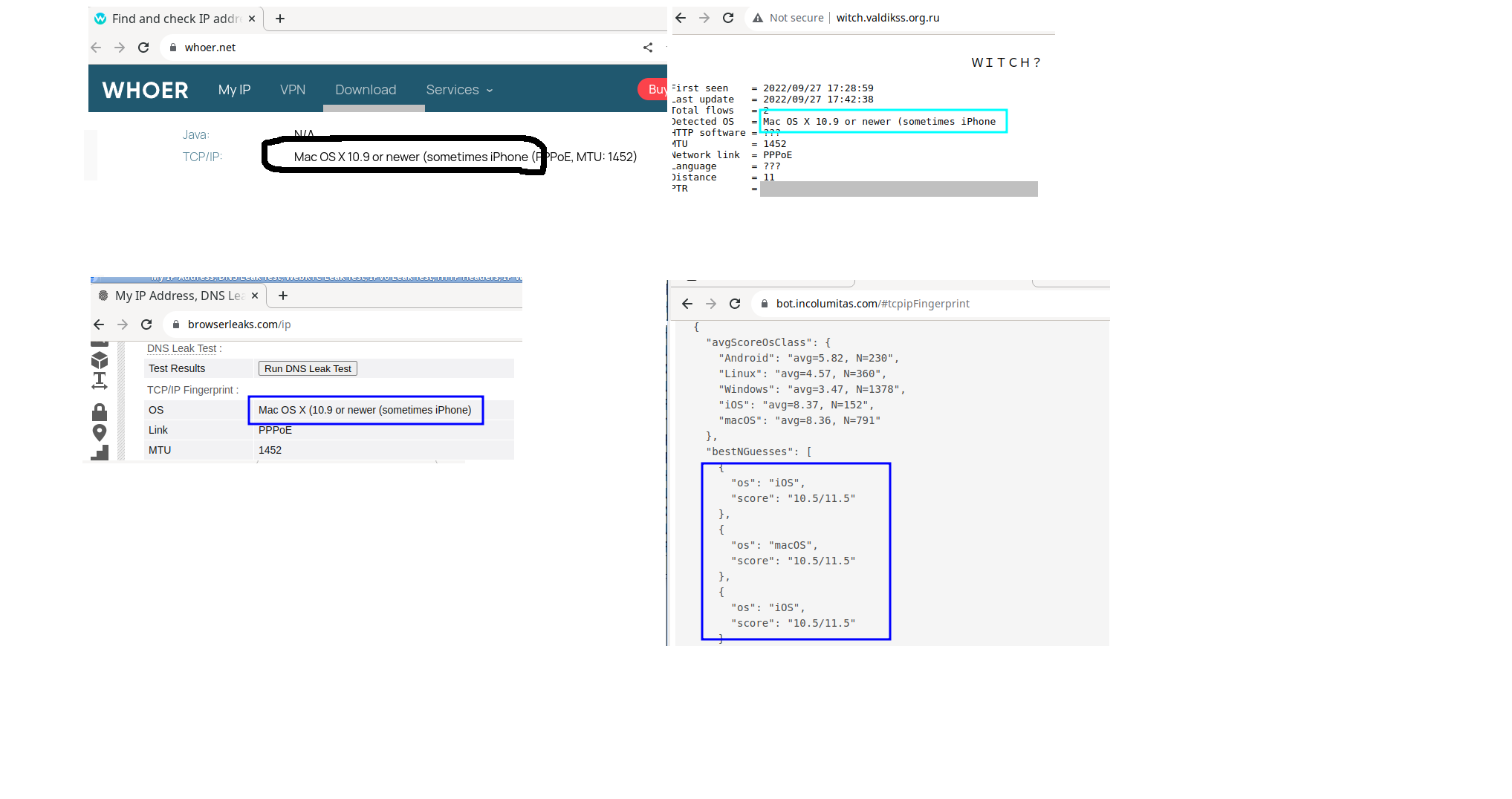
MacOSX
OSGENRE=macosx ; DETAILS_P0F=1
- incolumitas
{“Android”:5.39,“Linux”:4.4,“Mac OS”:11.3,“Windows”:2.4,“iOS”:11.05}
- valdik
Detected OS = Mac OS X 10.x;MTU = 1398;Network link = ???
OSGENRE=macosx ; DETAILS_P0F=2
- incolumitas
{ “Android”: 5.39, “Linux”: 4.39, “Mac OS”: 11.3, “Windows”: 2.42, “iOS”: 11.05 }
- valdik
Detected OS = Mac OS X 10.x ; MTU = 1398; Network link = ???
OSGENRE=macosx DETAILS_P0F=3
- incolumitas
{“Android”:5.39,“Linux”:4.42,“Mac OS”:11.35,“Windows”:2.44,“iOS”:11.06}
- valdik
Detected OS = Mac OS X 10.9 or newer (sometimes iPhone;MTU = 1398;Network link = ???
IOS
OSGENRE=ios ; DETAILS_P0F=1
- incolumitas
{“Android”:5.43,“Linux”:4.48,“Mac OS”:11.32,“Windows”:2.7,“iOS”:11.07}
- valdik
Detected OS = Mac OS X iPhone or iPad;MTU = 1398;Network link = ???
OSGENRE=ios ; DETAILS_P0F=2
- incolumitas
{“Android”:5.41,“Linux”:4.44,“Mac OS”:11.92,“Windows”:2.4,“iOS”:11.93}
- valdik
Detected OS = Mac OS X [generic];MTU = 1398;Network link = ???
Windows
OSGENRE=windows DETAILS_P0F=1
- incolumitas
{“Android”:5.01,“Linux”:4.24,“Mac OS”:2.89,“Windows”:13.66,“iOS”:2.78}
- valdik
Detected OS = Windows 7 or 8;MTU = 1398;Network link = ???
OSGENRE=windows DETAILS_P0F=2
- incolumitas
{“Android”:3.86,“Linux”:3.99,“Mac OS”:2.71,“Windows”:6.68,“iOS”:2.55}
- valdik
Detected OS = Windows 7 or 8;MTU = 1398;Network link = ???
OSGENRE=windows DETAILS_P0F=3
- incolumitas
{“Android”:4.19,“Linux”:4.25,“Mac OS”:2.91,“Windows”:12.57,“iOS”:2.81}
- valdik
Detected OS = Windows 7 or 8;MTU = 1398;Network link = ???
Android
OSGENRE=android DETAILS_P0F=1
- incolumitas
{“Android”:10.23,“Linux”:10.82,“Mac OS”:2.52,“Windows”:3.6,“iOS”:2.47}
- valdik
Detected OS = Linux (Android);MTU = 1398;Network link = ???